Introduction To Writing eBPF Programs for Linux SecurityIntroduction To Writing eBPF Programs for Linux Security
eBPF is a versatile tool for improving Linux kernel security. This guide shows you how to write eBPF programs and discusses potential challenges.

In recent years, the Extended Berkeley Packet Filter (eBPF) has become a powerful tool for cybersecurity professionals. Designed for network filtering and monitoring within the Linux kernel, eBPF has evolved into a versatile technology with diverse applications, including security enhancements.
In this article, I will provide a step-by-step guide on how to write eBPF programs to boost security measures in a Linux environment.
Understanding eBPF and Its Security Applications
eBPF is a game-changer in security technology. It allows users to run sandboxed programs within the Linux kernel (kernel land) without modifying it. While it started as a tool for network filtering, eBPF now supports a range of functions, including security monitoring and performance tracing.
Here are some key features of eBPF that enhance security:
1. Programmable kernel filtering
eBPF programs can inspect and filter network packets (Ethernet frames), system calls, and other kernel-land events in real time. This capability allows for precise control over security features.
2. Performance and efficiency
eBPF programs operate with minimal overhead, making them suitable for high-performance security monitoring without significantly affecting system performance.
3. Dynamic tracing
eBPF enables security professionals to dynamically trace and analyze system behavior, detect anomalies, and identify potential security vulnerabilities in real time.
Writing eBPF Programs
Let’s explore the practical aspects of writing eBPF programs for security.
Tools and libraries for eBPF development
Before writing eBPF programs, you must set up your development environment. Here are some useful open-source tools and libraries:
1. libbpf
Libbpf is a library that contains utilities for loading and interacting with eBPF programs from user space.
2. bcc (BPF Compiler collection)
This set of libraries and tools is valuable for creating, compiling, and loading eBPF programs. It also offers high-level libraries for Python (bpfcc) and Lua (bcc-lua).
To install bcc, use the following commands.
On Debian-based systems: sudo apt install bcc
On Fedora-based systems: sudo yum install bcc
3. Clang/LLVM
eBPF programs are written in a C-type language and compiled using the LLVM infrastructure in Clang.
Anatomy of an eBPF program
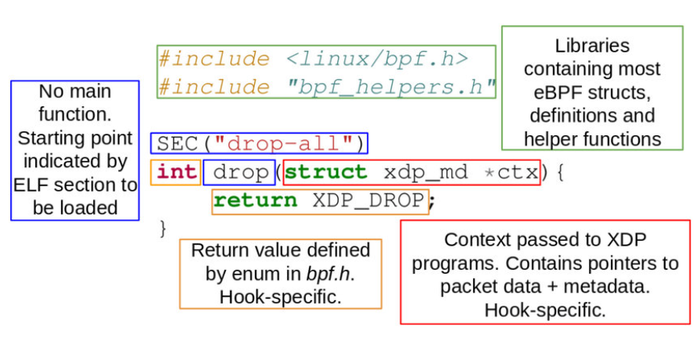
Credit: ResearchGate.net
Figure 1. The structure of an eBPF program.
eBPF programs have a few key components:
1. Maps
Maps are data structures facilitating communication between user space and kernel land components of an eBPF program.
2. Programs
These are the core eBPF programs, written in a restricted subset of the C programming language and then compiled into eBPF bytecode.
3. Verifier
The verifier ensures that the compiled bytecode is safe to execute within kernel land, preventing potentially malicious or unwanted code from affecting the kernel.
Writing your first eBPF program
Let’s walk through creating an eBPF program for security monitoring.
Note: The header files: <linux/bpf.h>, <linux/if_ether.h>, <linux/ip.h>, and <linux/in.h> are part of the Linux kernel headers installed on the system. You do not need to create them manually, but you do need to have the appropriate kernel headers installed. To install them, use your system’s package manager:
Debian:
sudo apt-get install linux-headers-$(uname -r)Red Hat:
sudo yum install kernel-headers-$(uname -r)Here is a simple C program for network packet filtering: https://gist.github.com/Grant-Knoetze/eef145e025f74af5265561e827a19243
Write the program using your preferred code editor:
#include <linux/bpf.h>#include <linux/if_ether.h>#include <linux/ip.h>#include <linux/in.h>SEC("filter")int filter_packets(struct __sk_buff *skb) { void *data = (void *)(long)skb->data; void *data_end = (void *)(long)skb->data_end; struct ethhdr *eth = data; struct iphdr *ip = data + sizeof(*eth); if (data + sizeof(*eth) + sizeof(*ip) > data_end) return 0; if (eth->h_proto == htons(ETH_P_IP) && ip->protocol == IPPROTO_TCP) { // Implement your filtering logic here // Example: Drop packets from a specific IP address if (ip->saddr == inet_addr("192.168.1.1")) return TC_ACT_SHOT; } return TC_ACT_OK;}char _license[] SEC("license") = "GPL";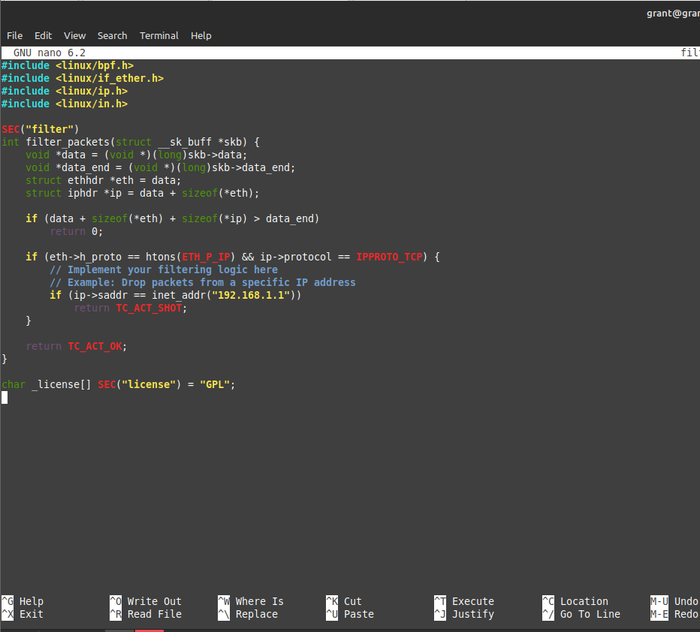
Figure 2. Here is a simple network packet-filtering eBPF program developed in Nano. It is ready for compilation.
Compiling and Loading eBPF Programs
Once you have written your eBPF program, you can compile it to eBPF bytecode using Clang and then load it into the kernel using bpftool or another utility provided by libbpf or bcc.
Compiling the eBPF program using Clang
1. Install Clang:
On Debian: sudo apt install clang
On Red Hat: sudo yum install clang
2. Compile the program:
Use the following command to compile your eBPF program:
sudo clang -O2 -target -c filter_program.c -o filter_program.oLoading the eBPF program
1. Install bpftool:
Follow the instructions at https://github.com/libbpf/bpftool to download and install bpftool.
2. Load the program:
Use the following command to load the compiled eBPF program into the kernel:
sudo bpftool prog load filter_program.o /sys/fs/bpf/filter_programAdvanced eBPF Techniques for Security
Here are a few advanced eBPF techniques for enhanced security.
1. eBPF for system call monitoring
eBPF can be used to monitor system calls made by processes. This technique helps security teams to audit and enforce policies, allowing them to detect and prevent malicious activities such as unauthorized file access and privilege escalation.
2. eBPF for intrusion detection and prevention
eBPF enables the creation of intrusion detection and prevention systems (IDPS) that analyze network packets and system calls in real time. By using eBPF directly in the kernel, you can reduce latency in threat detection and improve response capabilities.
3. eBPF for endpoint security
At the endpoint level, eBPF can monitor and enforce user security policies. This fine-grained control enhances protection against process execution, unauthorized file system access, and network communications, helping to detect and mitigate threats targeting endpoints within a network.
Challenges and Considerations
While eBPF is a powerful tool for enhancing security, there are a few points to consider.
1. Performance overhead
eBPF programs need to be well-optimized. Poorly optimized programs can increase performance overhead, affecting system responsiveness.
2. Security risks
Writing eBPF programs requires careful attention to security risks. Bugs or vulnerabilities in eBPF programs can compromise system security and integrity.
3. Kernel compatibility
eBPF features and APIs can vary between different kernel versions. Ensure compatibility by checking kernel support and, if necessary, using different eBPF implementations for various environments.
Main Takeaways
As eBPF technology evolves, security teams that understand the basics of eBPF programming can use its advanced features to strengthen defenses and improve response capabilities against cyber threats. Deploying custom eBPF programs directly within the kernel allows real-time monitoring, threat detection, and policy enforcement with minimal overhead. The increasing adoption of eBPF will provide more opportunities for security professionals to enhance their organizations’ security posture.
Additional Resources and Links
libbpf: https://github.com/libbpf
Clang/LLVM: https://clang.llvm.org/
Linux Foundation eBPF Documentation: https://ebpf.io/
ITPro Today Linux resources
About the Author
You May Also Like








.jpg?width=700&auto=webp&quality=80&disable=upscale)
