Securing Linux Systems with eBPF: The Future of In-Kernel Observability and SecuritySecuring Linux Systems with eBPF: The Future of In-Kernel Observability and Security
Learn about eBPF, its integration with Linux, applications in monitoring and securing systems, and more.
.jpg?width=1280&auto=webp&quality=95&format=jpg&disable=upscale)
Linux runs in IT infrastructure worldwide, including servers, cloud environments, virtual machines, and critical infrastructure. As the threat landscape changes and security threats become more sophisticated, the need for advanced security mechanisms has increased.
Extended Berkeley Packet Filtering (eBPF) is a technology advancing in-kernel observability and IT security. In this article, we will explore the fundamental theory of eBPF, how Linux interacts with this technology, eBPF’s applications in monitoring and securing Linux-based systems, and the available tools for enhancing security.
Introduction to eBPF and Its Capabilities
Extended Berkeley Packet Filtering is an innovative technology that augments the original Berkely Packet Filtering functionality, initially developed for packet filtering. eBPF allows user-defined programs and applications to execute directly from within the Linux kernel, providing broader applications beyond networking. This enhanced capability makes eBPF versatile for observability, performance monitoring, and security applications.
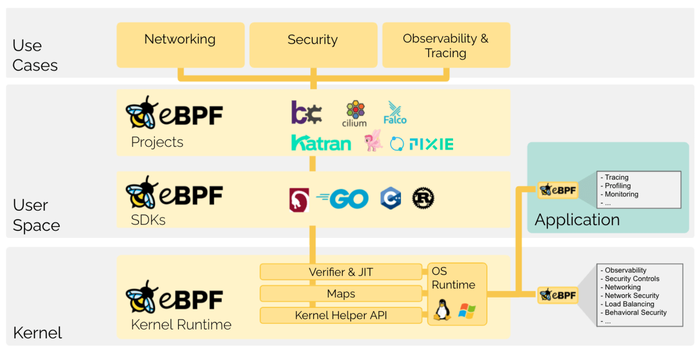
Credit: https://ebpf.io/what-is-ebpf/
Figure 1. An overview of how eBPF works.
eBPF allows programs written in a subset of C to be compiled into bytecode, verified, and loaded into the kernel. These programs run with the highest privileges within level zero of the protection rings. The eBPF verifier ensures the safety of the programs before execution.
Berkeley Packet Filtering allows network packets (ethernet frames) to be captured and filtered at the operating system level. For example, a tcpdump process may want to receive only packets that initiate a TCP connection; BPF filters ensure that only these packets are returned to the process, avoiding the need to copy unwanted packets from the kernel, which greatly improves performance. eBPF extends this functionality to support programs that need to analyze network traffic and perform other advanced tasks.
Background: Userland vs. Kernel Land
Just like other operating systems, Linux separates user space from the kernel. In a Linux system, users interact with the “userland,” where applications are easy to install and run since they don’t need to integrate deeply with low-level kernel or system processes. However, the separation has a major limitation: Userland applications struggle to collect data directly from the operating system. Only processes running in “kernel land” can do this. Kernel land is a protected system area where typically only processes critical to the operating system’s normal functioning are allowed to run.
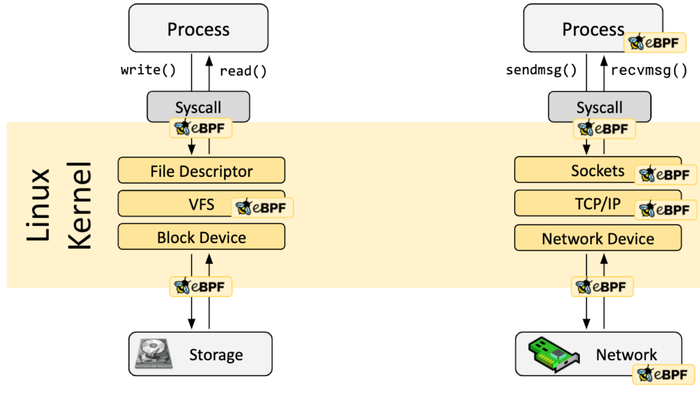
Courtesy of: https://ebpf.io/what-is-ebpf/
Figure 2. A kernel probe (kprobe) or user probe (uprobe) can be used to attach eBPF programs almost anywhere in the kernel or user applications.
Securely Programming Filters for Better Access
Developers usually bridge the gap between userland and kernel land by creating kernel features that securely expose data to userland applications. The main drawback to this approach is that it requires modifying the kernel, which is a massively complex platform and hard to change safely.
An alternative solution has traditionally been to create kernel modules that collect data from the kernel. System administrators can load the modules into kernel land after the kernel is already running, allowing low-level access without modifying the kernel. However, this method typically requires root-level access and can introduce security and stability issues if the modules are poorly designed. Additionally, these modules can increase the operating system’s resource usage.
The Benefits of eBPF
eBPF takes a unique approach to gaining low-level access to the kernel by providing an isolated, sandboxed environment. Despite being sandboxed, eBPF programs can still interact with the kernel components based on configured settings. This approach offers several benefits to teams needing insight into the operating system’s inner workings:
Simplicity: Loading eBPF programs is swift and easy, unlike directly modifying the kernel.
Security: eBPF programs are inherently secure because they are sandboxed from the rest of the operating system. They do not produce the same performance or security challenges that kernel modules typically introduce.
Efficiency: eBPF programs use very few system resources, meaning they have a minimal impact on the operating system’s performance.
eBPF and Network Observability
eBPF offers the most value in network observability, with use cases such as monitoring hardware performance and detecting security issues over the network. Modern applications often run across clusters of servers and in containers, serverless functions, and other infrastructure types that abstract applications from the host operating system. Traditionally, observing the network under these conditions required collecting and correlating data from multiple servers and dealing with containers that typically do not log network operations to the host OS and may store network-related data persistently.
System administrators have addressed these challenges by deploying a complex array of userland applications, including a network monitoring agent on each server and agents to collect network data from each container via service mesh, sidecar architecture, or similar approaches.
eBPF provides a much simpler and more elegant solution for network observability. With eBPF, teams can run kernel land programs that monitor and log network operations for all containers in clusters on a server. Doing so eliminates the need for deploying agents to each container while providing access to low-level networking data that containers cannot access unless running in privileged mode (not recommended, as it violates the principle of least privilege).
Thus, eBPF addresses core network visibility challenges in modern applications by providing a secure, simple, and efficient means of monitoring Linux-based endpoints.
Key Capabilities of eBPF
eBPF provides several capabilities that make it well-suited for enhancing modern application security.
High performance: eBPF programs run within kernel land, ensuring minimal overhead and high performance. This is key for real-time monitoring and security applications.
Flexibility: eBPF’s flexibility is partly due to its ability to attach multiple hook types within kernel land, making it versatile for diverse use cases such as network packet filtering and filesystem monitoring.
Safety: The eBPF verifier maintains the stability and security of the kernel by ensuring that loaded programs do not perform unsafe operations.
Extensibility: eBPF can be extended with data structures called “maps,” which exchange information between eBPF programs and userland applications. This enables the processing of complex data and policy enforcement.
Use Cases of eBPF in Security
The capabilities of eBPF make it an excellent tool for enhancing Linux system security. Here are some notable use cases.
Detecting anomalies
eBPF can monitor system activities like system calls, network traffic, and process behaviors to detect anomalies indicative of security threats. For instance, eBPF programs can track unusual network traffic patterns that might signal a Distributed Denial of Service attack or monitor file access to identify potential ransomware activity.
Monitoring system calls
Security teams can analyze application behavior closely by attaching eBPF programs to system call hooks. For example, monitoring system calls related to file operations helps detect unauthorized access or modifications to sensitive files.
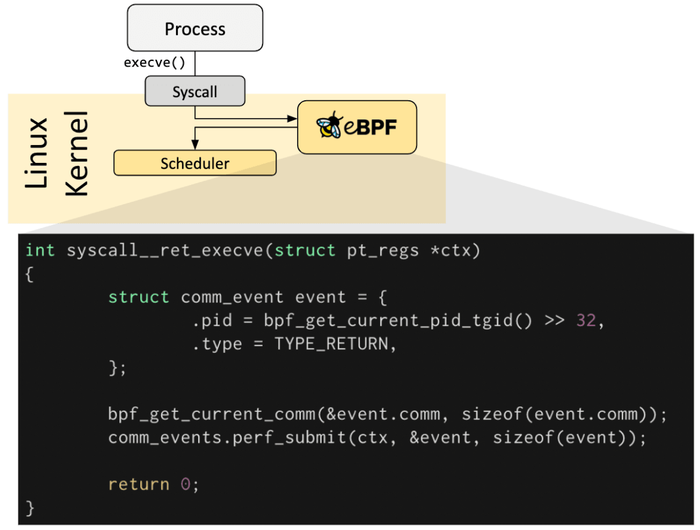
Credit: https://ebpf.io/what-is-ebpf/
Figure 3. The hook overview for system calls. Credit: https://ebpf.io/what-is-ebpf/
Network security
eBPF originated in networking, which makes it highly effective in network security. It enables advanced packet filtering, monitoring of network flows, and enforcement of security policies directly in kernel land. This capability allows real-time detection and mitigation of network-based threats.
Container security
With the widespread adoption of containerized environments, securing containers has become more of a concern. eBPF can monitor container activities, help enforce security policies, and detect anomalies within containerized applications. This is particularly valuable in Kubernetes environments, where eBPF provides visibility into network traffic and system calls at the container level.
Main Takeaway
eBPF is a powerful technology revolutionizing how system administrators and teams approach Linux system security. Its ability to execute custom programs within kernel land with minimal overhead offers unparalleled observability and control over system activities. With eBPF, security teams can effectively detect anomalies, monitor system calls, enforce network security policies, and secure containerized environments.
Additional Resources and Links
eBPF: https://ebpf.io/
ITPro Today’s Linux Resources
About the Author
You May Also Like








.jpg?width=700&auto=webp&quality=80&disable=upscale)
