Mastering File Permissions in LinuxMastering File Permissions in Linux
Here’s everything you need to know about setting file permissions in Linux. This guide covers both the GUI and command line approaches.

Linux is a widely used operating system favored by professionals and home users worldwide. It is well known for its strong security and integrity features.
In computer security, key concepts include confidentiality, integrity, and availability. When it comes to the computer’s file system, file permissions play a crucial role in securing sensitive information (confidentiality), preventing unauthorized modifications to files (integrity), and allowing appropriate access to files for authorized users (availability). In Linux, file permissions can be set using both the graphical user interface (GUI) and the command line in the terminal.
This article will explain how to set file permissions using the GUI and the terminal, enabling you to protect your system against unauthorized access and modifications. We will also examine how to use permissions symbolically and numerically.
What Are File Permissions in Linux?
In Linux, permissions control the access to files and directories for different types of users. There are three main permissions in Linux: read, write, and execute.
Read: Read permissions allow users to view the contents of a file, but they cannot edit or modify it. Read permissions do not grant users the ability to execute the file.
Write: Write permissions enable users to make changes to a file, such as adding new entries to a .CSV file. However, write permissions alone do not permit file execution.
Execute: Execute permissions authorize the user to run a file, which can be a program or script. This permission is required to execute the file’s code.
How Do We Use File Permissions?
We use file permissions to maintain the confidentiality, integrity, and availability of files and folders. File permissions allow us to manage access to these resources. File permissions can be set either through the GUI or from the terminal.
Using the ls Command To Visualize File Permissions
To visualize file permissions in Linux, we use the ls command, which stands for “list.” The ls command provides a detailed list of the folder’s contents. When using the -l flag with the ls command, it displays additional information, including permissions. Figure 1 shows an example of how the permission details are displayed in the terminal.

image001-1
Figure 1. The output of ls -l to the terminal.
In Figure 1, we can see 10 highlighted bits in the first column. The first bit indicates whether it is a file or a folder we are dealing with. A dash (-) represents a file, while the letter d indicates a folder. In Figure 1, the d in the first line of the first column indicates a directory (named volatility3), while the dash (-) in the second line represents a file.
Now, let’s take a closer look at the ls -l command output. In the first column, we see the sequence drwxr-xr-x. Notice that there are 10 bits in total.
Within the 10 bits, each bit represents a specific permission: read (r), write (w), and execute (x). In binary notation, a bit is considered enabled (set) if it is represented by a letter (r, w, x). Conversely, a dash (-) signifies a disabled bit. Therefore, by examining the 10 bits, we can determine the file permissions for different roles.
These permissions are divided into sets of three. Starting from the left, the first trio represents the permissions for the file owner, the second trio represents the permissions for the group the file belongs to, and the third trio represents the permissions for all other users.
Set Permissions Based on Role in Linux
Linux offers us the ability to set permissions based on specific roles. There are three main roles: owner, group, and all other users and groups.
Owner role
The owner role refers to the person who owns the file. When we look at the nine permission bits displayed by the ls -l command in a directory, the first set of three bits is reserved for the owner. These bits determine the permissions and can be set to any combination of read (r), write (w), and execute (x).
In Figure 2, we can see that the file volatility3_install.sh has read, write, and execute permissions set for the owner. In the terminal, the owner role is represented by the character “u”.

image002-1
Figure 2. The first trio of bits represents owner permissions for the file. Here, grant is the owner.
Group role
The next trio of bits represents the group to which the file belongs. In Figure 3, the file belongs to the grant group. In the command line, the group role is represented by the character “g”.

image003-1
Figure 3. The second trio of bits represents group permissions.
All other users and groups role
The last trio defines the permissions for the “all other users and groups” role. Figure 4 illustrates these permissions. In the terminal, “all other users” is denoted by the character “o”.

image004-1
Figure 4. The trio of bits that set the permissions for the “all other users and groups” role.
Modifying Permissions in Linux
Permissions can be modified for files and folders both through the GUI and the terminal. Let’s examine how to set permissions in the GUI first and then how to set permissions in the terminal.
Modifying File Permissions in the GUI
Modifying file permissions in the GUI is straightforward. Right-click on a given file, select Properties, and then navigate to the Permissions table, as can be seen in Figures 5 and 6.

image005-1
Figure 5. The Properties option when a file is right-clicked on.

image006-1
Figure 6. Where to modify permissions in Properties in the GUI.
In the GUI, we can change permissions according to the role (owner, group, and others).
Modifying File Permissions in the Terminal
Inside the Linux terminal, we can change the permissions using the chmod (change mode) command. This powerful command allows us to change permissions for the three role types: owner, group, and all other users. To indicate the role, we use the following symbols: “u” for the owner, “g” for the group, and “o” for all other users.
To add permissions, we use the plus symbol (+), and to remove permissions, we use the minus symbol (-). After specifying the role in the command, we need to include the actual permission as a parameter. In the Linux terminal, those are “r” for read permissions, “w” for write permissions, and “x” for execute (run) permissions.
So, to add write permissions for the group role, the command would look like this:
sudo chmod g+w The command's output can be seen in Figure 7, where it displays that the write permission has been successfully added to the group role. Additionally, the group role also has read and execute permissions set.
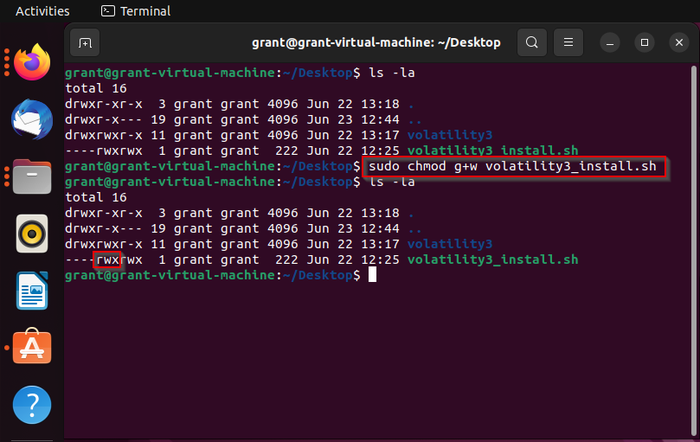
image007-1
Figure 7. The result of the sudo chmod g+w volatility_install.sh command.
To remove write permissions from the group role, you can use the following command:
sudo chmod g-w The output can be seen in Figure 8, where the group role has had the write permission removed.

image008-1
Figure 8. The results of the sudo chmod g-w volatility_install.sh command.
In a single command, you can modify multiple permissions for a specific role. For example, the following command grants read, write, and execute permissions for the owner role:
sudo chmod u+rwx The result is shown in Figure 9. The owner has been successfully granted read, write, and execute permissions for the specified file (volatility3_install.sh).

image009-1
Figure 9. The results of the sudo chmod u+rwx command.
Alternatively, you can add a single permission to multiple roles simultaneously. The command would look like this:
sudo chmod ugo+r The command adds the read permission to the owner, group, and all other users and groups roles. The results of this command can be seen in Figure 10.
You can also reverse the process and remove a permission from multiple roles at once. For example:
sudo chmod ugo-rThis command removes the read permission from the owner, group, and other users and groups roles.

image010-1
Figure 10. The results of adding and then removing the read permission for and from multiple roles simultaneously.
This format of using rwx and ugo to denote permissions and users in the chmod command is known as Symbolic Format. However, there is another format, Numeric Format, which offers a faster and simpler way to change permissions. In the Numeric Format, we assign numeric values to each permission (read, write, and execute).
Here are the numerical equivalents for permissions: 4 for read (r), 2 for write (w), and 1 for execute (x). To set permissions, we add these values for each group we want to affect.
For example, if we want to add read (4) and execute (1) permissions, we add those numbers together, resulting in 5. This means that the role we are modifying will have read and execute permissions. We can illustrate this by setting the permissions for the owner role using the number 5. The command will look like this:
sudo chmod 5 When setting permissions numerically, the positions from left to right represent the owner, group, and all other users roles. For example, if you want to set read and write permissions for the owner role; read permissions for the group role; and read, write, and execute permissions for the all other users and groups role, you can use the following command:
sudo chmod 637In this case, you add the numerical values for the desired permissions: 4 for read, 2 for write, and 1 for execute. Adding these values for each role results in the numerical representation 637.
Additionally, if you want to set all permissions for all roles, you can use the number 7, which represents the sum of 4 (read), 2 (write), and 1 (execute). The command would look like this:
sudo chmod 777 Figure 11 shows the outcome of executing the command, where all permissions have been granted to all roles.

image011-1
Figure 11. The results of the sudo chmod 777 volatility3_install.sh command.
In contrast, we can revoke permissions numerically using the “0” character from our numbers set. To remove all permissions from all roles, the command would look like this:
sudo chmod 000 The outcome can be seen in Figure 12, where all permissions have been revoked for all roles.
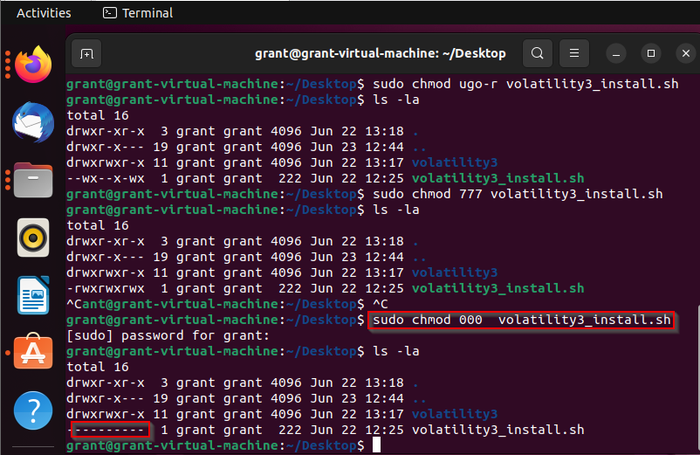
image012
Figure 12. The results of the sudo chmod 000 volitility_install.sh command.
Final Thoughts
Modifying file permissions in Linux can be easily accomplished through the GUI or the terminal. Linux users need to know how to modify file permissions effectively. This article aims to serve as a starting point in your journey of mastering file permissions in Linux.
Frequently Asked Questions (FAQ)
Q: How do I set file permissions in Linux?
A: To set file permissions in Linux, you can use the chmod command in the terminal. Alternatively, you can use the GUI by right-clicking on the file, selecting Properties, and then adjusting the permissions.
Q: What are the different types of file permissions in Linux?
A: The three main permissions in Linux are read, write, and execute. These permissions determine whether a user can view, modify, or run a file.
Q: What are the risks of having incorrect file permissions in Linux?
A: The risks of having incorrect file permissions include the possibility of unauthorized persons gaining access to sensitive information. Incorrect permissions may allow unauthorized users to read, modify, and execute files and programs. Proper file permissions provide granular control over who can access what and for what reason.
Additional Resources and Links
Here are several links to additional resources to help you on your way.
Linux documentation
The official Linux Kernel Documentation: https://docs.kernel.org/
The Linux Foundation Filesystem Hierarchy Standard: https://refspecs.linuxfoundation.org/FHS_3.0/fhs/index.html
IT Pro Today Linux resources
About the Author
You May Also Like








.jpg?width=700&auto=webp&quality=80&disable=upscale)
