Using Windows 10 Sandbox to Test Potentially Malicious ApplicationsUsing Windows 10 Sandbox to Test Potentially Malicious Applications
Windows 10 Sandbox: What to watch for--and out for--when testing potentially malicious code.
November 1, 2021
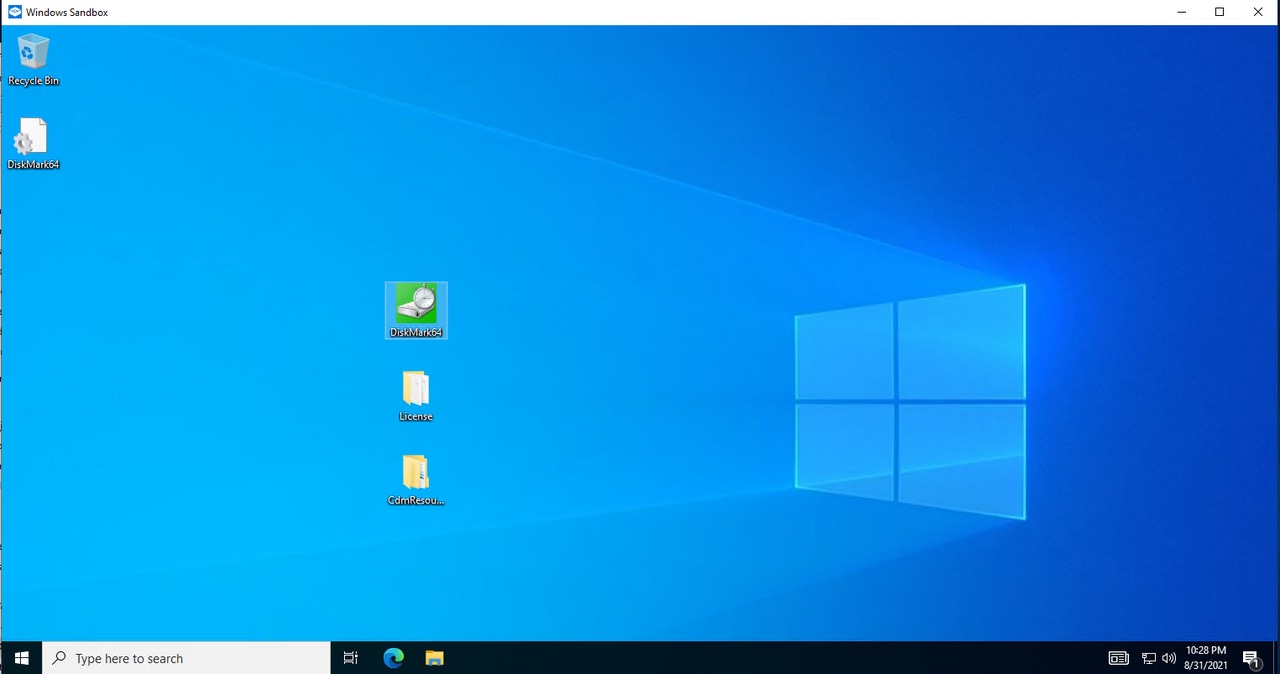
The Windows 10 Sandbox acts as an isolated environment that can be used for testing potentially malicious code. Nothing run inside the sandbox environment should harm the primary operating system, and the sandbox is automatically reset to a pristine state each time it is used. Even so, there are a few aspects of the Windows 10 Sandbox that may be cause for concern.
The Windows 10 Sandbox is based on container technology, so, to use it, your PC must support hardware virtualization. You can enable the Sandbox by entering the Control command at the Windows Run prompt to open the Control Panel. Now, click on Control, followed by Turn Windows Features On or Off. This will cause Windows to display a list of optional features. Select the Windows Sandbox option and click OK. Windows will now install the Sandbox feature and prompt you to reboot the system.
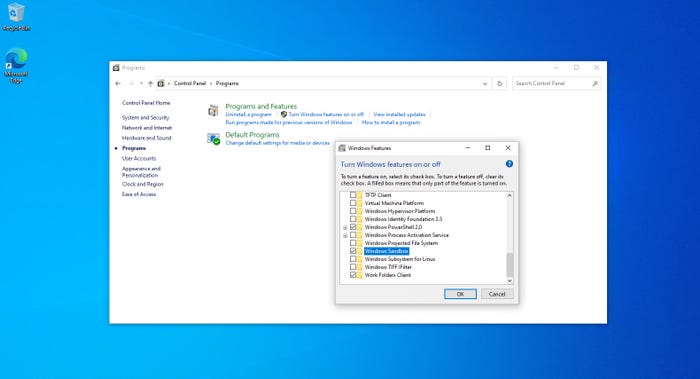
Windows 10 Sandbox 1
Figure 1
Select the Windows Sandbox option and click OK.
When the system restarts, you can access the Windows 10 Sandbox by selecting the Windows Sandbox option from the Start menu. You can see what the Windows Sandbox looks like in Figure 2. As you can see, the Sandbox looks almost exactly like a Windows 10 virtual machine. Unlike a virtual machine, however, you don’t have to manually allocate hardware resources to the sandbox, nor do you have to install a Windows operating system. All of that is done automatically.
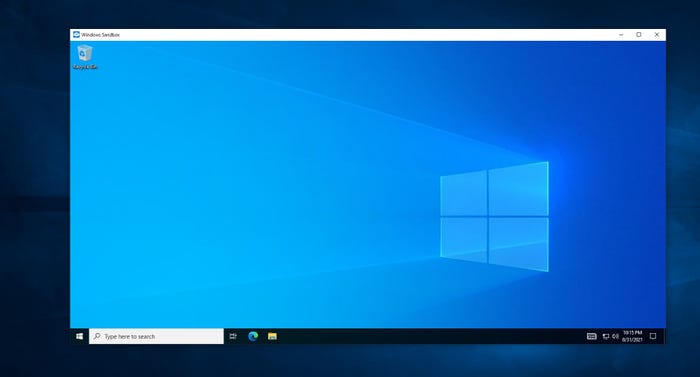
Windows 10 Sandbox 2
Figure 2
The Windows Sandbox looks a lot like a virtual machine.
Once the sandbox is up and running, you can use it to test potentially malicious code. There are two main ways that you can do this. The first option is to cut and paste files from your desktop into the sandbox. Just right-click on the files that you want to test, and select the Copy option from the shortcut menu. Next, right-click inside of the sandbox and choose the Paste option. This will cause the files to be pasted into the sandbox. You will then be able to run those files inside of the sandbox environment. The figure below shows an example of a few files that I pasted into the sandbox.
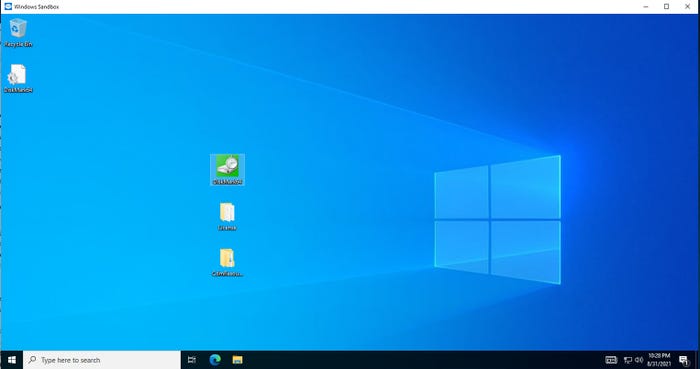
Windows 10 Sandbox 3
Figure 3
You can paste files into the sandbox for testing purposes.
As convenient as it might be to cut and paste files into the sandbox, it is also possible to copy files that exist within the sandbox and paste them into the system’s primary operating system. It is at least theoretically possible that malware could exploit this capability and escape the sandbox environment. Thankfully, a Group Policy setting can help to prevent clipboard sharing. I will explain more about this Group Policy setting later on.
The other way to test potentially malicious code in the Windows 10 Sandbox is to open a Web browser and download whatever it is that you want to test. Obviously, allowing the sandbox to have network access so that it can access the internet poses certain risks. Microsoft attempts to mitigate these risks by placing the sandbox onto an isolated subnet. Even so, it is still possible to open a Command Prompt window and use the Net Use command to map a network drive to resources on your private network, as shown in Figure 4. Some of the IP addresses are partially obscured in the figure, but the figure clearly illustrates that it is possible for the sandbox environment to access your private network.
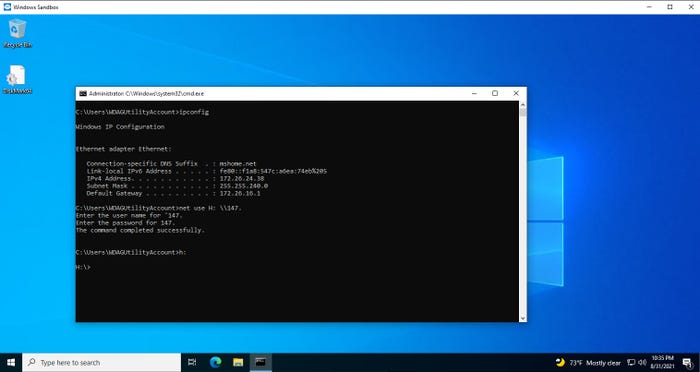
Windows 10 Sandbox 4
Figure 4
The Windows Sandbox can gain access to your private network.
Windows 10 Build 20161 and higher include several Group Policy settings that will allow administrators to place additional restrictions on the Sandbox, including preventing network access. These settings, which are shown in Figure 5, are also available in Windows 11. As you can see, they allow you to disable audio, clipboard sharing, networking, printer sharing, vGPU sharing and video input in the sandbox environment. These settings, when properly used, should go a long way toward making the Windows Sandbox more secure.
You can find the Sandbox-related Group Policy settings within the Group Policy Editor at: Computer Configuration Administrative Templates Windows Components Windows Sandbox.
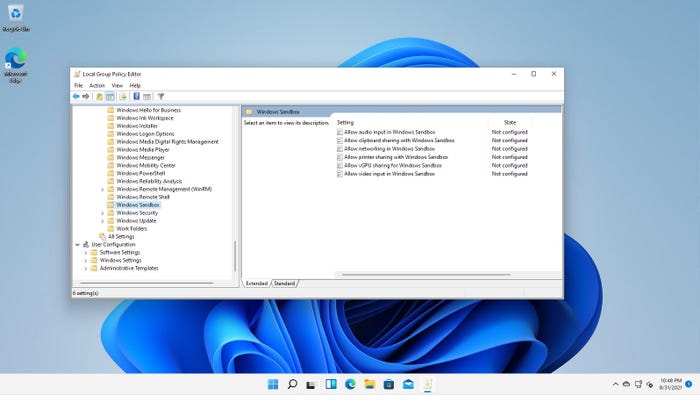
Windows 10 Sandbox 5
Figure 5
Microsoft is introducing several Group Policy settings to make Windows Sandbox more secure.
About the Author
You May Also Like








.jpg?width=700&auto=webp&quality=80&disable=upscale)
