How to Sign PowerShell Scripts, Part 3How to Sign PowerShell Scripts, Part 3
This guide explains how to sign PowerShell scripts. In Part Three, you will learn the final steps of the process.
July 7, 2022

So far in this guide, we have learned to prepare our certificate authority (CA) and acquire a certificate that can be used to sign PowerShell scripts. Before I show you how signing works, I want to walk you through one more simple procedure that will help the process run smoothly.
Table of Contents
Part 3: Use the Certificate to Sign a PowerShell Script
Trusting the CA
In Part Two, I mentioned that when you visit the CA website, you might receive an error message that says there is a problem with the site’s certificate. This happens because the CA is untrusted as a certification authority. It isn’t really a problem, but it does mean that we will continue to receive warning messages. That being the case, I want to show you how to make your PC trust the CA.
From the domain-joined system where you will eventually sign PowerShell scripts, go back to the CA website that you used in Part Two (https://< your CA name >/certsrv). This time, when you reach the main screen, click the Download a CA Certificate, Certificate Chain, or CRL link. On the following screen, click the Download a CA Certificate link, then save the certificate to your hard disk.
Now enter the MMC command at the Windows Run prompt. When the console opens, choose the Add / Remove Snap-ins option from the file menu. Select the Certificates snap-in, then click Add. When prompted, choose the Computer Account option and click Finish, followed by OK.
Navigate through the console tree to Certificates | Trusted Root Certification Authorities | Certificates. Right-click on the Certificates container and select All Tasks | Import from the shortcut menus, as shown in Figure 1. Just follow the steps to import the certificate that you downloaded a moment ago. The computer will now trust the CA.

PowerShell Signing 3-1
Figure 1. Right-click on the Certificates container and choose All Tasks | Import from the shortcut menus.
Create a Sample PowerShell Script
The next thing you will need is a sample PowerShell script to test the code signing process on. For the purposes of this article, I have created a script called HelloWorld.ps1. This script contains a single line of code. When executed, the script causes the words, Hello World, to display on the screen.
Modify the Execution Policy
Since our goal is to test the effectiveness of signing a PowerShell script, let’s set the execution policy to AllSigned. This will prevent any unsigned scripts from running. In Figure 2, you can see that my script ran fine prior to changing the execution policy, but it does not run once the execution policy has been changed. Incidentally, you can change the execution policy by using this PowerShell command:
Set-ExecutionPolicy AllSignedIf you need to remove all restrictions from the machine, you can use this command:
Set-ExecutionPolicy Unrestricted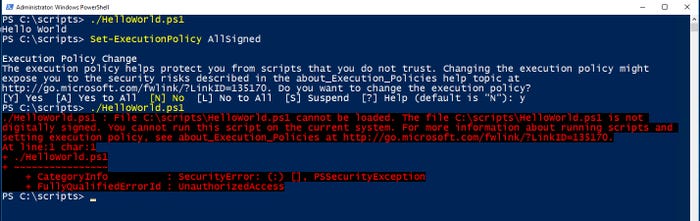
PowerShell Signing 3-2
Figure 2. The AllSigned execution policy prevents unsigned scripts from running.
Verify Your Signing Certificate
Now we must make sure PowerShell recognizes the signing certificate we installed (as was explained in Part Two). To do so, run this command:
Get-ChildItem Cert:CurrentUserMy -codesign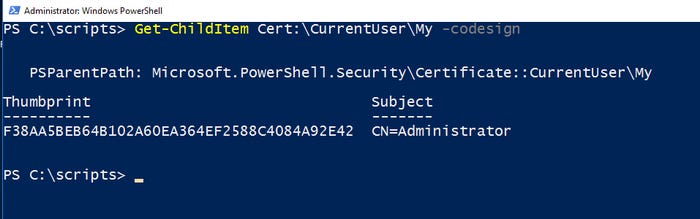
PowerShell Signing 3-3
Figure 3. PowerShell recognizes the existence of the code signing certificate.
It’s time to sign the sample PowerShell script. The technique that I am about to show you assumes that there is only one signing certificate present. If there are multiple certificates, you must modify the technique to specify the certificate you want to use. You will notice that the command I use ends with [0]. This tells PowerShell to use the certificate in location 0, which is the first certificate on the list.
Here is the command:
Set-AuthenticodeSignature .HelloWorld.ps1 @(Get-ChildItem Cert:CurrentUserMy -CodeSign)[0]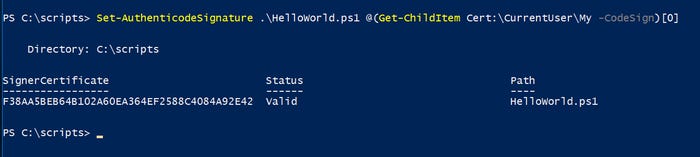
PowerShell Signing 3-4
Figure 4. The script has been signed.
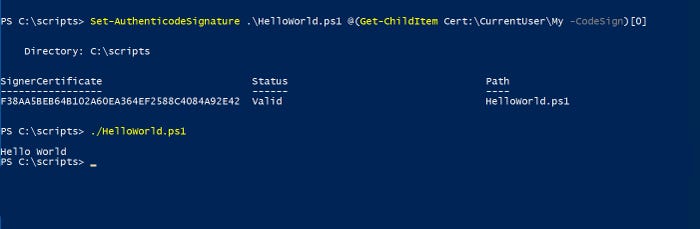
With the PowerShell script signed, there are two ways to confirm that the signing process was successful. The first option is to simply execute the script. As you can see in Figure 5, the script runs without issue.
PowerShell Signing 3-5
Figure 5. The signed script is executed.
The other way to verify that the script has been signed is to open the script and look at its contents. In Figure 6, notice that a signature block has been appended to my script.

PowerShell Signing 3-6
Figure 6. This is what a signed script looks like.
It is worth noting that if the script is modified, it will need to be resigned.
About the Author
You May Also Like








.jpg?width=700&auto=webp&quality=80&disable=upscale)
