Security and Compliance in Office 365: ReportingSecurity and Compliance in Office 365: Reporting
Within the navigation for the Security & Compliance center, you are able to view extensive reports for Office 365. To access the reports, expand the Reports blade and then select Dashboard. Once the dashboard opens you will see that currently it does not contain many items at all.
April 4, 2017
Within the navigation for the Security & Compliance center, you are able to view extensive reports for Office 365. To access the reports, expand the Reports blade and then select Dashboard.

Once the dashboard opens you will see that currently it does not contain many items at all.

This page is simply the placeholder for more reports to be displayed and made available in the future. To actually run reports within the Security & Compliance center, you select any of the four sections from the Search & Investigation blade.

The one that is of most use, is the Audit log search, where you get detailed access on what end users may have been doing within the site.

From within the search, screen the first step is to select the Activities that you wish to search and see.

This list is extensive and covers the following categories of activities:
File and folder activities
Sharing and access request activities
Synchronization activities
Site administration activities
Exchange mailbox activities
Sway activities
User administration activities
Azure AD group administration activities
Application administration activities
Role administration activities
Directory administration activities
eDiscovery activities
Power BI activities
Microsoft Teams activities
As you can see this is an extensive list. If we select Directory administration activities category is will select all activities.

Selecting the required activities, will then allow us to perform a search based on that and dates. When a search is performed, the results are returned showing the user performing the activity, as well as the object being updated or modified, along with the account if it is being modified too.

The Audit log search is really powerful and allows Administrators to really drill down and inspect the usage of their Office 365 tenant.
You can also script these searches if needed allowing greater flexibility as needed. To do this, the Search-UnifiedAuditLog command using the following format:
Search-UnifiedAuditLog -EndDate -StartDate [-Formatted ] [-FreeText ] [-IPAddresses ] [-ObjectIds ] [-Operations ] [-RecordType ] [-ResultSize ] [-SessionCommand ] [-SessionId ] [-UserIds ]
More details of this can be found here: https://technet.microsoft.com/en-us/library/mt238501(v=exchg.160).aspx
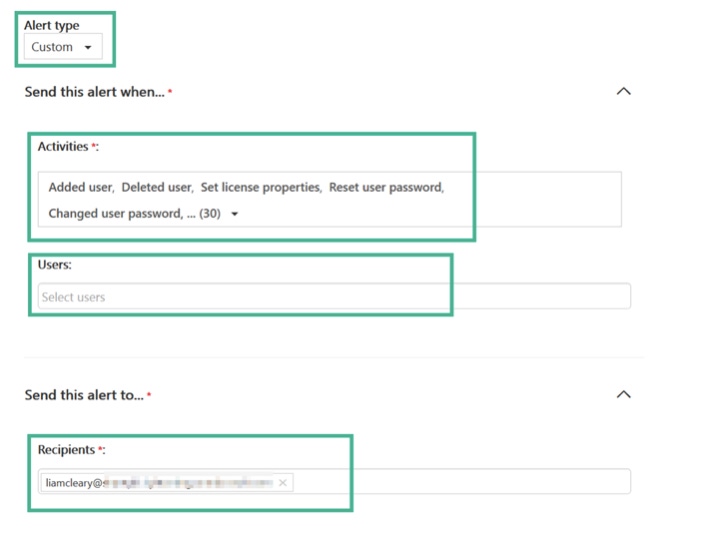
Though it is great to be able to perform searches, personally I love the ability to create the filters, perform the searches, but even better create that and then create an alert from that. After creating the search syntax and performing the search, you can simply click + New alert policy button. This will slide out the wizard for creating alerts, with it set to custom by default.

The activities are prepopulated from the search syntax, the recipient is assigned to you, you can then also select specific users to filter the results even further. Once this is all done, you can then save this. Once saved it shows up in the Alerts section of the Security & Compliance center.
To learn more about searching the audit log, you can head over to the Office site.
About the Author
You May Also Like






.jpg?width=700&auto=webp&quality=80&disable=upscale)
