How Microsoft LAPS Can Help Improve Endpoint SecurityHow Microsoft LAPS Can Help Improve Endpoint Security
Here’s a quick guide to using Microsoft LAPS, which stores the local administrator password securely in Active Directory.
June 29, 2020
Although the local Administrator account in Windows 10 has its place, it can also pose a security risk. After all, desktops are often provisioned with identical administrator passwords. Thankfully, Microsoft makes available a tool called the Local Administrator Password Solution, or Microsoft LAPS, that solves this problem by storing the local administrator password securely in Active Directory. That way, passwords can be protected by ACLs and are accessible only to authorized users.
Microsoft LAPS is not currently included in the Windows Server operating system. I expect this to change over time, but, for right now, you will have to download and install LAPS before you can use it. You can download Microsoft LAPS here.
The download consists of an MSI installer. Microsoft LAPS needs to be deployed on your domain controllers, but you will also need to install the MSI file onto the domain members whose passwords you want to manage. You can, of course, manually install the MSI package onto those machines, but it is typically going to be easier to push the package out using Group Policy or by using an application management tool.
The deployment process isn’t overly difficult, but it isn’t quite as intuitive as you might expect. To get started, run the MSI file that you downloaded. The installer is GUI-based, and you will need to choose which components you want to install, as shown in Figure 1. The computer that you are using to configure LAPS will need all of the optional components.

LAPS 1
Figure 1
You will need to select the components that you wish to install.
Once you finish installing the LAPS software, you will need to configure it. The first step in the configuration process involves extending the Active Directory schema. Schema extensions are generally safe, but it is a good idea to create an Active Directory backup just in case.
To extend the Active Directory schema, open an elevated PowerShell window and enter the following commands:
Import-Module AdmPwd.psUpdate-AdmPwdAdSchemaYou can see what this process looks like in Figure 2.

LAPS 2
Figure 2
You will need to extend the Active Directory schema to make LAPS work.
The next step in the process is to delegate permission for Microsoft LAPS to interact with your domain-joined computers, using the command below:
Set-AdmPwdComputerSelfPermission –Identity *After you have delegated the necessary permissions, you can verify the delegation by entering this command:
Find-AdmPwsExtendedRights -Identity *If you look at Figure 3, for example, you can see that the Domain Admins group has been granted extended rights to manage local passwords stored in the Active Directory.

LAPS 3
Figure 3
The required permissions have been delegated.
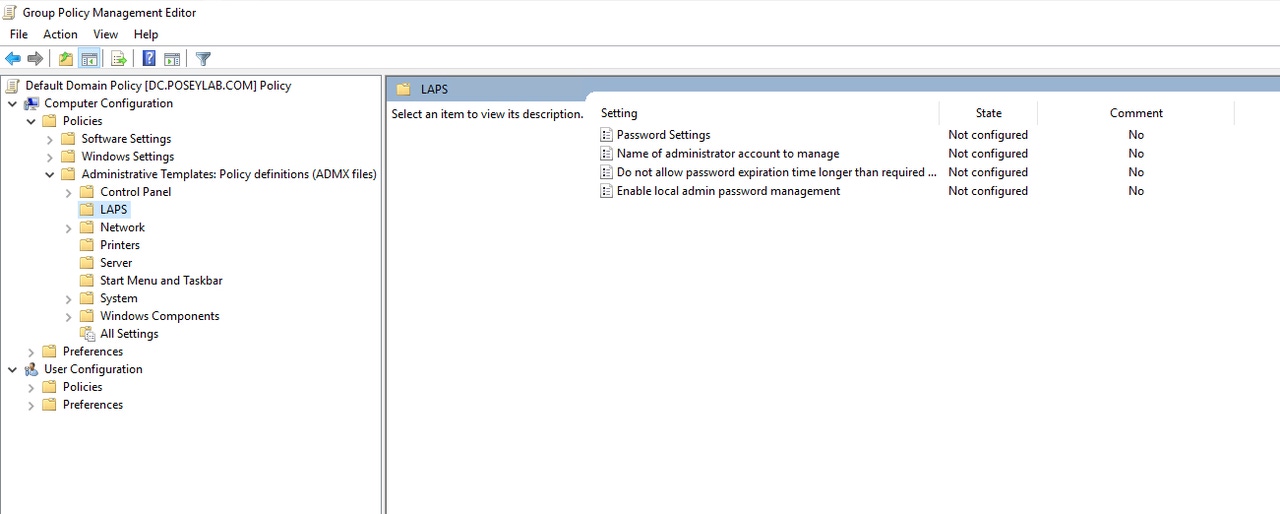
The next thing that you will need to do is enable Microsoft LAPS at the Group Policy level. To do so, open the Group Policy Management Editor and navigate through the console tree to Computer Configuration | Policies | Administrative Templates | LAPS. If you don’t see the LAPS container, then reinstall the LAPS software on the machine that you are using to edit the group policy and be sure to include the Group Policy component. You can see the Microsoft LAPS-related settings in Figure 4.

LAPS 4
Figure 4
These are the Group Policy settings available for managing Microsoft LAPS.
As you can see in the figure, none of the Group Policy settings is enabled by default. To use Microsoft LAPS, you will need to enable the Enable Local Admin Password Management setting. You can use the other Group Policy settings to establish a password policy for the domain joined computers.
Remember that even when you have configured the Group Policy settings, Microsoft LAPS will work only after you have installed the LAPS software onto your domain-joined machines. (You don’t have to install the management tools.) Once you have configured a computer or two, it can be helpful to test LAPS to make sure it is working as intended. You can do this through PowerShell using the command shown below:
Get-AdmPwdPassword -ComputerName So, as you can see, LAPS has the potential to greatly improve the security of the domain-joined computers on your network.
Read more about:
MicrosoftAbout the Author
You May Also Like








.jpg?width=700&auto=webp&quality=80&disable=upscale)
