Product Review: CloudPassage HaloProduct Review: CloudPassage Halo
CloudPassage Halo is a Software as a Service (SaaS) offering that provides automated, scalable security protection for Windows and Linux servers that form a cloud infrastructure.
February 21, 2013
Managing Windows Server security can be a challenge once your server estate grows past a handful of devices. If you're not afraid of the command line, Windows Server 2012 provides effective management for larger server farms through Windows PowerShell. However, working exclusively with the command line can be a stiff learning curve for many administrators. In addition, getting quick results and interpreting data without a graphical interface isn't always ideal when you need to respond quickly to changing situations.
CloudPassage Halo is a Software as a Service (SaaS) offering that provides automated, scalable security protection for Windows and Linux servers that form a cloud infrastructure. Halo monitors security, alerts you about suspicious events, and provides strong firewall protection and multifactor authentication across your entire server farm.
Security as a Service
Halo runs a small, lightweight daemon (service) on each server that you want to monitor, which in turn connects to the Halo Grid. The grid runs in the cloud. It continuously collects data from each daemon and pushes policies to each monitored server. Events are recorded in a log in the management portal, which is called the Halo Portal. Halo can alert administrators immediately if a critical security event occurs.
To make security management as easy as possible, Halo uses server groups to assign policies. For example, you might place all web servers in a Halo server group and assign common firewall settings. GhostPorts provide a two-factor authentication mechanism that requires a user's Halo Portal password, plus a one-time password sent to the user's mobile phone. No special hardware is required, but Halo supports YubiKey hardware/software two-factor authentication in case it's needed.
Installing Halo
Installing and setting up Halo was simple. After I registered on CloudPassage's website, I logged on to the Halo Portal and downloaded the service daemon. I ran the installer on the server I wanted to protect and entered the domain registration code supplied on the download page.
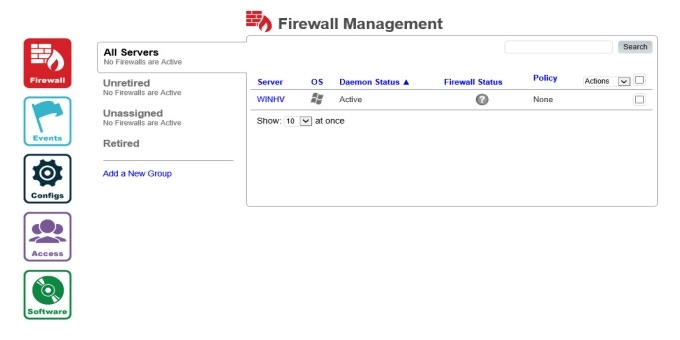
Next, I logged on to the Halo Portal, where I saw the server listed on the Firewall Management tab, as shown in Figure 1. The first thing that struck me about the web management portal is the clean and simple lines, which make it very easy to navigate without a steep learning curve.
Figure 1: Firewall Management Tab of the Halo Portal
Server groups form the basis of all Halo configurations, so my first task was to create a new group named Standard in which to place my server. There's a link conveniently placed on the Halo Portal start screen to create a group. Selecting the Add a New Group link pops up a separate dialog box while graying out the background, ensuring that your attention is focused on the task at hand.
When you don't have any policies defined, creating a group is simply a matter of giving the group a name, optionally specifying a Server Tag, and clicking Save. You then move the server to the new group by selecting the server in the All Servers group, choosing Move Server(s) from the Actions drop-down menu, and selecting the group. If you specify a Server Tag when you create a group, you don't need to manually move any new servers into that group. When you install the daemon on a new server, you just specify the Server Tag and the server will then be automatically added to the matching server group.
Configuring Halo Firewall Policies
After the group is populated with a server, you can create and apply some policies. Halo groups can have only one policy applied to them at a time. So, if you need to apply multiple firewall rules, they must all be listed in the same policy. It's important to understand that Halo is applying Windows Firewall rules and not its own firewall technology. As such, you'll be able to see Halo firewall rules in the standard Microsoft Management Console (MMC) Windows Firewall snap-in on servers managed by Halo. The rules applied by Halo are marked as CloudPassage rules to make them easy to identify.
When applying the first firewall policy, I was a little concerned that I might accidently lock myself out of the server by applying firewall rules through the Halo Portal. I noticed that apart from the standard core networking firewall rules that are present in Windows by default, all other default inactive inbound and outbound firewall rules were deleted. However, Halo adds default outbound rules for the daemon to ensure that access to the Halo Grid is always maintained.
As a simple test, I created an inbound firewall rule for secure POP3 from any IP address and blocked all other inbound access. There's a list of built-in network services to choose from, or you can define your own. Likewise, you can define your own IP address ranges and network interfaces. After I created the new policy, I edited the Standard group I created earlier and applied the new firewall policy. It took about a minute before the new policy became active on the server, which was noticeable as I was kicked out of my remote desktop session because I specified to block all incoming connections that didn't match the POP3 rule. To rectify this, I simply added another rule to the firewall policy to allow incoming RDP traffic. Within a minute, I was able to get remote desktop access to my server again. The default heartbeat for the daemon is 60 seconds but can be increased up to 15 minutes.
Using GhostPorts
GhostPorts stops hackers from continuously scanning for open ports. It works by authorizing employees using two-factor authentication through the Halo Portal. It determines the user's source IP address and then modifies the server's firewall according to the GhostPorts rules that apply to the user, giving access to services and ports only from traffic identified to be from the user's IP address.
Halo Portal users need to be individually enabled to use GhostPorts. This is done by editing the user details in Site Administration under Settings. You can choose to use SMS codes or YubiKey. After the phone number of the user is entered, the user must confirm it by logging on to the Halo Portal again and entering a code sent to his or her phone. It should be noted that you can create standard user accounts in Halo Portal purely for the purposes of opening GhostPorts.
For this review, I tested SMS two-factor authentication. I enabled GhostPorts for my own administrative user account in the Halo Portal and changed the firewall rule I previously created to let inbound access for RDP port 3389 from any source IP address to this GhostPorts user (i.e., myself). This meant that in order to make a remote desktop connection to the server, I had to be logged on to the Halo Portal and authenticated using my Halo password and a code sent to my mobile phone by SMS.
After applying the rule, I first made sure that remote desktop access to my server was denied. I then re-authenticated on the Halo Portal. Once logged on, I clicked Open GhostPorts in the top right of the Halo Portal and confirmed that I wanted to send an authentication code to my mobile phone. After you enter the code into the Halo Portal, it displays the source IP addresses for the ports that will be opened according to the firewall policy and a note that you should wait for a minute before trying to access the services. You get four hours of open access, or you can manually close ports by selecting the Close GhostPorts link in the top right of the Halo Portal.
Exploring Other Halo Features
Halo can log and alert you on what it calls special events. By default, all servers are covered by the global events policy, which contains a list of events such as Server shutdown and Server moved to another group. Some events are currently Linux only.
Alert profiles are easy to set up. You choose the kind of events you want to know about and the users to notify. Those users will then be alerted by email if the events occur.
Halo can run configuration checks to ensure servers meet certain conditions, such as running ACL checks on directories or confirming that a user has a password. However, all these checks apply to Linux only. At the time of this writing, CloudPassage was planning these features for Windows in early 2013. File integrity checking is also included in beta form.
Simple, Strong Security
One benefit of managing Windows Firewall using Halo is that no matter what you do from the Halo Portal, it's impossible to lock yourself out of a server completely—something that's quite possible if you're working with the MMC Windows Firewall snap-in directly. Although firewall policies should always be carefully planned, mistakes do happen. It's crucial not to be locked out of a remote server that can't be physically accessed for quick repair.
Halo is a good fit for small and large organizations alike. It's very easy to implement and provides advanced functionality in a form that can be easily deployed without a large outlay in infrastructure and hardware. Halo is a good option for any organization that needs to simplify but also strengthen cloud security.
About the Author
You May Also Like






.jpg?width=700&auto=webp&quality=80&disable=upscale)
