Changing UAC Behavior for Windows Server 2012 R2 and Windows 8.1
Learn how to modify the UAC behavior for Windows Server 2012 R2 and Windows 8.1.
February 26, 2014
User Account Control or UAC has been a feature of Windows systems for a long while. In Windows Vista, UAC was one of the underpinnings that really destroyed adoption of the OS. Hardware and software compatibility were big factors, too, but Vista's UAC configuration bewildered end users because the UAC alert seemed to pop-up for every action.
UAC's concept is a good one, ensuring applications and services can't take administrator-level permission without consent. When changes need to be made to the computer a prompt will request permission to do so, requiring an administrator-level account to allow. If the logged on user is not at the administrator level, an administrator or equivalent is required to unlock the requesting function. The intent is to prevent malicious software from being installed or to make changes to the computer.
In Windows Server 2012 R2 and Windows 8.1, UAC is much kinder, but it can still be bothersome when performing specific tasks. For example, say you are just setting up and configuring a Windows Server 2012 R2 instance and creating VMs by installing software. As an administrator, the process could go much quicker without having to grant permissions every couple minutes.
If you feel comfortable with the software you are installing, you can alter how UAC behaves and eliminate the pop-ups altogether.
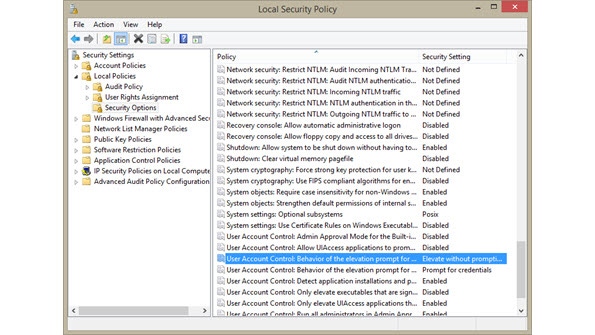
From the Search screen, search for 'secpol.msc' and run it.
In the console tree, open Local Policies, and then click Security Options.
In the contents pane, double-click User Account Control: Behavior of the elevation prompt for administrators in Admin Approval Mode.
Select Elevate without prompting in the list, and then click OK.
Close the Local Security Policy window.
About the Author
You May Also Like






.jpg?width=700&auto=webp&quality=80&disable=upscale)
