10 Ways To Harden Your Linux Containers Against Attacks10 Ways To Harden Your Linux Containers Against Attacks
Learn practical strategies for protecting containerized applications on Linux.

Containerization technology has transformed how we build and deploy software by bundling applications with their dependencies into lightweight, portable units. Tools like Docker and Kubernetes have streamlined the management and orchestration of containerized applications across cloud and on-premises infrastructures, making them a cornerstone of IT infrastructure. But while containers provide some isolation for the apps they house, they aren't foolproof when it comes to security. Misconfigurations can lead to vulnerabilities that could jeopardize your host system or entire cloud setup.
This guide breaks down best practices for securing containerized apps on Linux, helping you reduce risks while getting the most out of containerization.
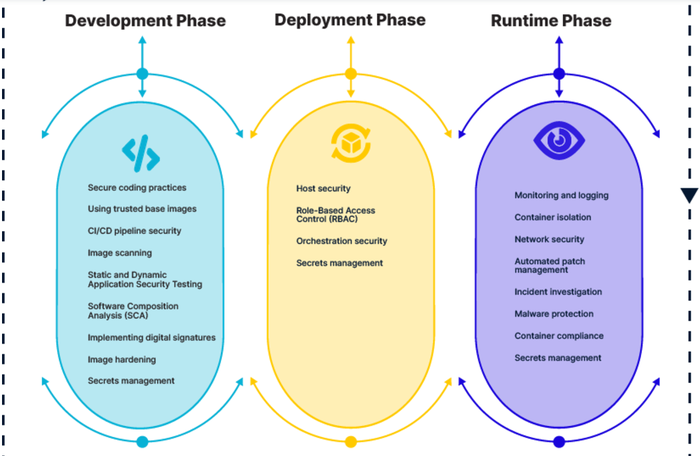
CREDIT: Aquasec
Figure 1. Container security requires deploying a variety of protections across various stages of the software development lifecycle.
The Container Threat Model
Before we jump into security best practices, we should highlight the threats specific to containers. Unlike virtual machines, which each have a dedicated kernel, containers share the host’s kernel. This dependency on the host system means that any vulnerability in the container engine, runtime, or the host kernel can lead to privilege escalation and compromise.
Here are a few common threats to know:
Container breakout: Attackers exploit flaws to escape a container and access the host system.
Image vulnerabilities: Containers built from images with outdated libraries, insecure code, or malicious code can cause breaches.
Unrestricted network access: Containers running as root can inadvertently give attackers high-level access to the host system.
By recognizing these threats and taking steps to address them, you can significantly shrink the attack surface of your containerized apps.
1. Secure Your Container Images
The first step to locking down your containers is securing their base images. Think of the base image as the foundation for your containerized application.
Use trusted base images
One of the largest risks to container security is using unverified or insecure base images. If your base image has vulnerabilities, every container built from it inherits those problems.
Use official or trusted images: Always use official images from verified sources, such as Docker Hub or other verified container registries.
Update your base images: Update base images regularly to ensure they include the latest security patches and fixes.
Use minimal base images: Opt for minimal base images, such as Alpine Linux or Distroless, which have fewer components and thus reduce the potential attack surface.
2. Scan Images for Vulnerabilities
Even trusted images can contain outdated libraries or misconfigurations, so it is crucial to scan them regularly.
Use image scanning tools like Clair, Anchore, or Docker Security Scanning to identify potential issues in your container images. Automate the scanning process within your CI/CD pipeline to catch vulnerabilities early.
Additionally, you should remove unused dependencies and libraries from images to reduce attack vectors and minimize the risks of exploitation.
3. Sign and Verify Images
Image signing ensures unauthorized parties have not tampered with or altered container images.
You can sign your images with tools like Docker Content Trust or Notary. These tools verify the authenticity of images before you pull them from the registry.
Additionally, you should implement image policy controls to prevent deploying unsigned or untrusted images.
4. Implement Strong Access Controls
Avoid running containers as root, as it is one of the most dangerous practices in container security. If an attacker breaks out of a root container, they can gain control of the host system.
Run containers as non-root users: Always specify a non-root user in the Dockerfile (using the USER directive) or configure it at runtime (e.g., docker run --user).
Use namespaces and cgroups: Isolate container processes from the host’s kernel and other containers by leveraging namespaces and cgroups.
Implement role-based access control (RBAC)
RBAC ensures that only authorized users or services can access Linux containers, nodes, and networks, helping to limit the exposure and prevent unauthorized access.
Use RBAC policies in Kubernetes: In Kubernetes, define RBAC policies to control which users and services can access specific resources.
Enforce least privilege access: Grant the minimum permissions necessary for each user or service.
Secure CLI and API access
Attackers can exploit Docker or Kubernetes APIs for privilege escalation and compromise of your Linux environment.
Use authentication and authorization mechanisms: Implement strong authentication, such as certificates from trusted authorities, to verify and restrict access to the API.
Enforce encrypted communication: Require encrypted communication over TLS for all API calls to ensure that sensitive information is transmitted securely.
5. Use Container Isolation Mechanisms
Since containers share the host kernel, you must properly isolate containers from the host system. You can achieve this using Linux namespaces and cgroups.
Namespaces isolate system resources such as the file system, network, and process trees. Properly configured namespaces to limit a container’s access to the host system.
Cgroups restrict the amount of system resources (CPU, memory) containers can use. Configure cgroups to prevent resource exhaustion attacks and ensure each container operates within its allocated limits.
Use Seccomp, AppArmor, and SELinux
Security modules like Seccomp, AppArmor, and SELinux add extra layers of isolation by enforcing security policies at the kernel level.
Use Seccomp: Seccomp restricts the system calls a container can make, reducing the attack surface.
Configure AppArmor or SELinux policies: Enforce process-level restrictions on containers by configuring AppArmor or SELinux policies to control what each container can access and modify.
Apply default or custom security profiles: Use default security profiles for containers or create custom profiles based on the principle of least privilege.
6. Secure Networking for Containers
Limiting container-to-container communication can reduce threats such as lateral movement, where attackers move between containers to escalate their attack.
Use network policies: Define and enforce network policies to control which containers can communicate with each other.
Encrypt network traffic
All communication between containers, services, and the host should be encrypted to prevent attackers from intercepting sensitive information.
Use Transport Layer Security (TLS): Secure communication between containers and external services by using TLS.
Implement Mutual TLS (mTLS): Use mTLS to authenticate and encrypt traffic between services inside the container network.
7. Secure Container DNS
DNS spoofing attacks can redirect container traffic to malicious sites, potentially compromising the security of your containers.
Use DNSSEC: Implement DNS Security Extension (DNSSEC) to protect against DNS spoofing and ensure the authenticity of DNS responses.
Use Trusted DNS Servers: Ensure container DNS requests are resolved through secure and trusted DNS servers.
8. Implement Logging and Monitoring
Centralized logging is crucial for containerized applications, as logs provide valuable insight into application behavior and potential security incidents. However, since containers are often short-lived, log retention can be challenging.
Use logging tools: Adopt tools like Fluentd, Logstash, or ELK stack to aggregate logs from containers and hosts.
Ensure immutability: Make sure that logs are immutable and stored securely to prevent tampering by attackers.
Monitor for abnormal behavior
Detecting suspicious activity early on can help identify threats before they escalate.
Use security monitoring tools: Use tools like Falco or Sysdig to detect abnormal behavior, such as privilege escalation attempts or unexpected process executions, that may indicate a breach.
Deploy EXR and SIEM systems: Implement Extended Detection and Response (XDR) and Security Information and Event Management (SIEM) systems to correlate container activity with other system events.
9. Update and Patch Systems
Any vulnerability in the host system can expose all containers to potential attacks. The host system must be updated and patched regularly to protect against known vulnerabilities.
Opt for a minimal host operating system, such as CoreOS or Flatcar Linux, to reduce the attack surface.
10. Establish backup and disaster recovery procedures
Regular backups and disaster recovery planning will help you recover quickly from incidents such as ransomware attacks or container compromises.
Systematic backups: Back up container configurations and data regularly. Use version control systems like GIT to track container configurations, allowing you to revert to a previous state when necessary.
Create a disaster recovery plan: Develop and test a disaster recovery plan to prepare for the worst-case scenarios, such as container or host compromises. Simulate recovery scenarios to ensure your team can respond to emergencies effectively.
Secure backup storage: Set up backup procedures that include encrypted backups and secure storage to prevent tampering or unauthorized access.
Main Takeaway
Securing containerized apps on Linux takes a multi-layered approach. You will need to focus on image management, network configuration, access controls, and keeping an eye on everything with continuous monitoring. By following the tips in this guide, you can mitigate risks and strengthen the security of your containerized environments.
About the Author
You May Also Like








.jpg?width=700&auto=webp&quality=80&disable=upscale)
